目 录CONTENT

我的动态
-
2025/05/12 11:21:38
配置私有话对象存储minio访问,使用Ningx反向代理
user www-data; worker_processes auto; pid /run/nginx.pid; include /etc/nginx/modules-enabled/*.conf; events { worker_connections 768; # multi_accept on; } http { server { listen 80; server_name 域名; listen 443 ssl; ssl_certificate /root/ssl/your.crt; ssl_certificate_key /root/ssl/your.key; location / { proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; proxy_set_header Host $http_host; proxy_connect_timeout 300; # Default is HTTP/1, keepalive is only enabled in HTTP/1.1 proxy_http_version 1.1; proxy_set_header Connection ""; proxy_pass http://127.0.0.1:9000; } } server { listen 80; server_name 域名; listen 443 ssl; ssl_certificate /root/ssl/your.crt; ssl_certificate_key /root/ssl/your.key; location / { proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; proxy_set_header Host $http_host; proxy_connect_timeout 300; proxy_http_version 1.1; proxy_set_header Upgrade $http_upgrade; # 支持 WebSocket proxy_set_header Connection "upgrade"; # 支持 WebSocket proxy_pass http://127.0.0.1:9001; } } }0 0 -
2025/04/11 18:37:39
给k8s配置代理。拉取dockerhub镜像
sudo mkdir -p /etc/systemd/system/containerd.service.d/ sudo tee /etc/systemd/system/containerd.service.d/http-proxy.conf <<EOF [Service] Environment="HTTP_PROXY=http://你的ip:端口/" Environment="HTTPS_PROXY=http://你的ip:端口/" Environment="NO_PROXY=localhost,127.0.0.1,192.168.0.0/16,10.0.0.0/8,172.16.0.0/12,.svc,.cluster.local" EOF # 重启containerd sudo systemctl daemon-reload sudo systemctl restart containerd0 0 -
2024/11/18 15:06:35
ubuntu上安装k8s命令补全工具
sudo apt install -y bash-completion echo "source <(kubectl completion bash)" >> .bashrc source ~/.bashrc1 0 -
2024/11/12 15:04:01
Linux安装node_exporter采集本地数据
useradd -M -s /usr/sbin/nologin prometheus mkdir /prometheus chown prometheus:prometheus -R /prometheus/ wget https://github.com/prometheus/node_exporter/releases/download/v1.8.2/node_exporter-1.8.2.linux-amd64.tar.gz tar -xvf node_exporter-1.8.2.linux-amd64.tar.gz -C /prometheus/ mv /prometheus/node_exporter-1.8.2.linux-amd64 /prometheus/node_exporter cat <<EOF> /etc/systemd/system/node_exporter.service [Unit] Description=node_exporter Documentation=https://prometheus.io/ After=network.target [Service] User=prometheus Group=prometheus ExecStart=/prometheus/node_exporter/node_exporter Restart=on-failure [Install] WantedBy=multi-user.target EOF systemctl enable --now node_exporter.service systemctl status node_exporter.service1 0 -
2024/11/12 15:00:28
Nginx反向代理常规配置
cat <<'EOF'> /etc/nginx/nginx.conf worker_processes 1; events { worker_connections 1024; } http { include mime.types; default_type application/octet-stream; sendfile on; keepalive_timeout 65; server { listen 80 default_server; server_name _; # Redirect all HTTP requests to HTTPS return 301 https://$host$request_uri; } server { listen 443 ssl; server_name 【域名】; client_max_body_size 1024m; ssl_certificate 【公钥文件路径】; ssl_certificate_key 【私钥文件路径】; location / { proxy_pass 【代理的地址+端口】; proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; } } } EOF systemctl enable --now nginx systemctl restart nginx1 0 -
2024/11/12 14:52:56
ubuntu刷新DNS
sudo systemd-resolve --flush-caches sudo systemctl restart systemd-resolved1 0 -
2024/11/08 10:54:09
解决3-xui面板安全问题,防止明文传输被GFW扫描,并切配置nginx代理以及https自动续签。
1、使用ssh连接远程服务器,并将远程主机端口映射到本地端口,通过ssh加密的形式访问,避免直接使用明文传输。
ssh -L 88:localhost:8080 root@远程主机地址 -p 222、登录到远程主机配置3-xui,项目在github上。
bash <(curl -Ls https://raw.githubusercontent.com/mhsanaei/3x-ui/master/install.sh)面板端口:8080
安装完成后,面板会提示端口以及路径,记录webBasePath: /路径。使用本地浏览器打开。假设得到的反馈如下:
root@localhost:~# x-ui settings The OS release is: ubuntu [INF] current panel settings as follows: username: fsdfdfdfc password: fdfdfefef port: 8080 webBasePath: /kjkflkdsjfkld/本机浏览器打开:http://localhost:88/kjkflkdsjfkld/ 登录面板修改webBasePath、用户名和密码、配置监听域名。我这边使用nginx做了代理,所以去掉了webBasePath。
3、远程主机配置nginx
命令:apt install nginx -y
配置nginx主配置文件
cat <<'EOF'> /etc/nginx/nginx.conf worker_processes 1; events { worker_connections 1024; } http { include mime.types; default_type application/octet-stream; sendfile on; keepalive_timeout 65; server { listen 80 default_server; server_name _; # Redirect all HTTP requests to HTTPS return 301 https://$host$request_uri; } server { listen 443 ssl; server_name 域名; client_max_body_size 1024m; ssl_certificate /root/xxx.pem; ssl_certificate_key /root/xxx.key; location / { proxy_pass http://127.0.0.1:8080; proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; } } } EOF systemctl enable --now nginx systemctl restart nginx4、默认x-ui面板使用明文传输,安装后会给出一个提示连接地址,即http://ip+端口。这个地址会被GFW扫描。因此,我们禁用外部连接本机的8080端口,只允许使用nginx来代理访问本机的8080。nginx配置了https加密。因此本地需要配置防火墙来实现。
sudo ufw enable sudo ufw default allow incoming sudo ufw deny 8080 sudo ufw allow from 127.0.0.1 to any port 8080 sudo ufw status verbose 执行反馈结果如下: root@localhost:~# sudo ufw status verbose Status: active Logging: on (low) Default: allow (incoming), allow (outgoing), disabled (routed) New profiles: skip To Action From -- ------ ---- 8080 DENY IN Anywhere 8080 ALLOW IN 127.0.0.1 8080 (v6) DENY IN Anywhere (v6)5、为nginx配置一个域名自动续签。需要提前在 https://httpsok.com 上配置好了解析。命令如下:
curl -s https://get.httpsok.com/ | bash -s klzrBDNP921aH6Lizn1z6、最后使用工具检测远程主机的8080端口是否能被外部访问以及443端口是否可行。正常情况下,8080端口被决绝。443端口被允许。
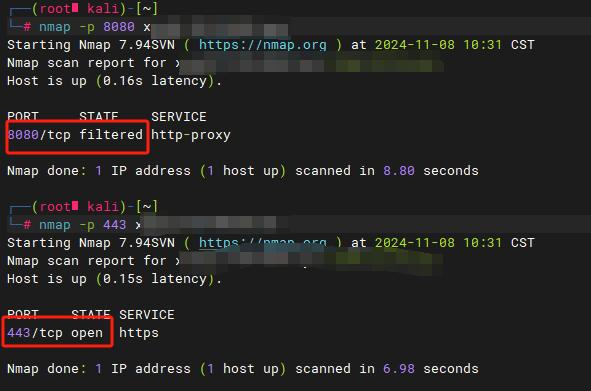
nmap -p 80 域名或者IP nmap -p 443 域名或者IP telnet 域名或者IP 80 telnet 域名或者IP 4431 0 -
2024/11/04 14:25:40
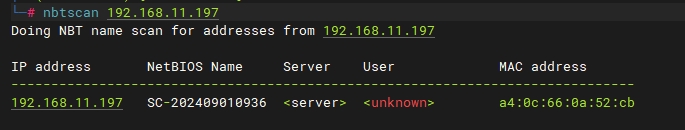
使用kali linux 查找ip对应的主机名和MAC地址:
┌──(root㉿kali)-[/etc/docker]
└─# nbtscan 192.168.11.197
Doing NBT name scan for addresses from 192.168.11.197
IP address NetBIOS Name Server User MAC address
------------------------------------------------------------------------------
192.168.11.197 SC-202409010936 <server> <unknown> a4:0c:66:0a:52:cb
 2 0
2 0